Encryption is a great way to secure the data and allow only authorized users to access it. And if you are not an authorized user, then you sit with a bunch of gibberish data that means nothing to you. What if there comes a situation wherein you are not allowed to access the data, but you can work on the data? Sounds unusual, but there are instances wherein the user is not concerned with the actual value of the encrypted data, but is interested in getting the output when some operation is performed on the data. In such cases, Functional Encryption comes handy.
Public Key Encryption(PKE)
We are familiar with the traditional Public Key Encryption(PKE), where we have a set of a public key(PK) and private key or secret key(SK) which we use for encrypting and decrypting a message. So, considering our traditional entities, Alice and Bob (who for some reason do a lot of cryptographic data exchange) data can be encrypted using the PK and the other entity can decrypt the data using their SK.
Encryption: c = f(m, pk)
Decryption: m = f(c, sk)
where,
m = message,
c = cipher text (encrypted message),
pk = public key,
sk = secret keyDrawback with PKE
The main drawback with PKE is that the decryption is "All or Nothing." In a sense, if Bob has the secret key(SK), then he can decrypt the entire message, and if not, then he is left with a sequence of encrypted text that is of no use to him.
But as we discussed earlier, what if you want to work with the data without accessing the actual values of it. We shall see how Functional Encryption can be used here.
Functional Encryption(FE)
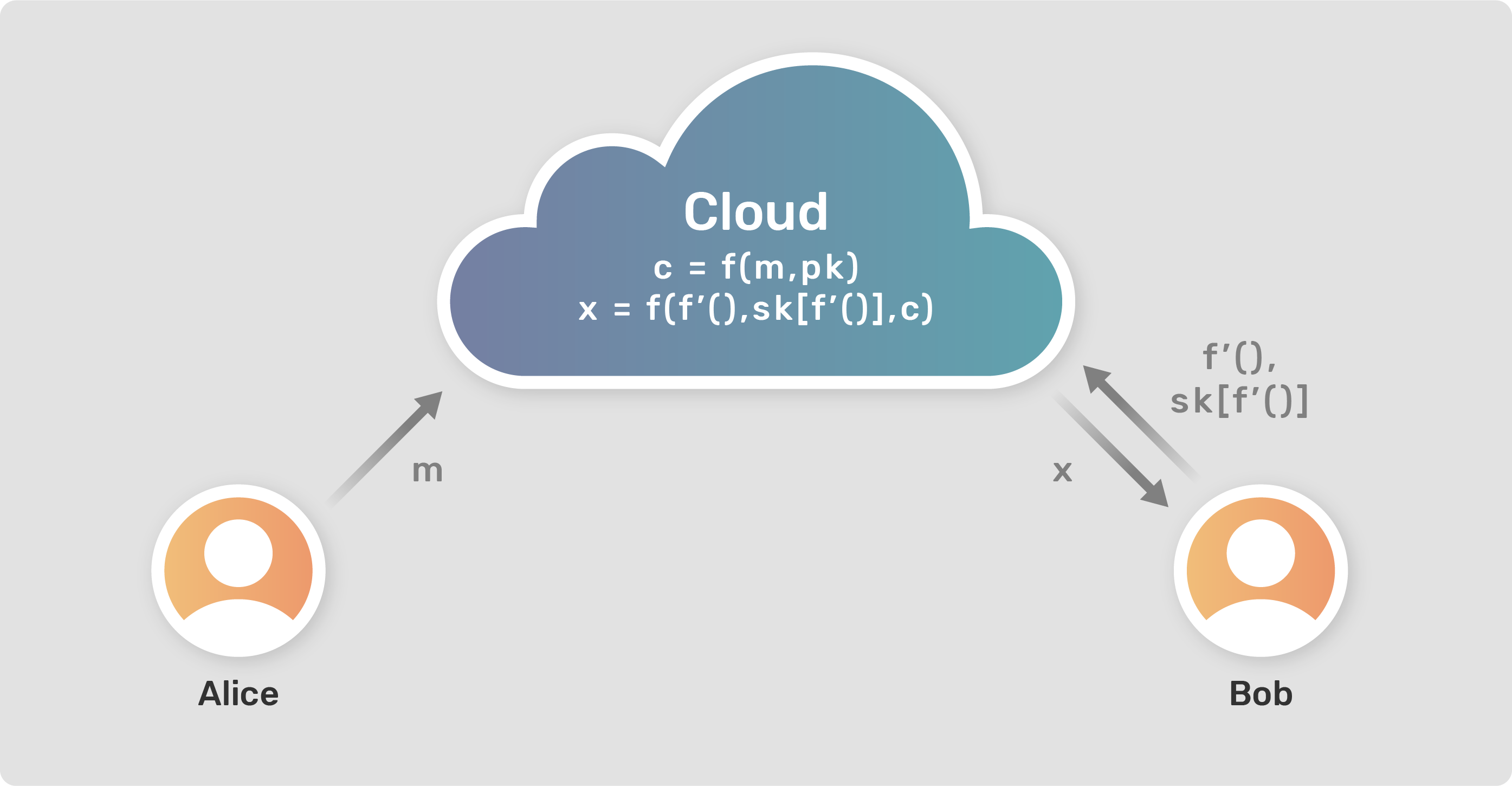
Functional Encryption(FE) allows one to get the output of the function performed on the data. Let us consider an example where Alice holds data a = 3, b = 5. Now, Bob wants to know the value of (a+b), but a and b are encrypted. So, Alice provides access to Bob to compute a function on the encrypted variables a and b. In this way, Bob would get the result of his function in decrypted form without even accessing the decrypted values of the variables.
Encryption: c = f(m, pk)
Decryption: x = f(c, f'(), sk[f'()])
where,
m = message or data
c = cipher text (encrypted data)
x = decrypted output of function f'()
f'() = any function
pk = public key
sk[f'()] = secret key for function f'()The implementation of above mathematical expression of FE is represented in Figure 1. Alice and Bob being the two parties involved in the data exchange and the operations are performed on a secure cloud server.
Functional Encryption(FE) VS Fully Homomorphic Encryption(FHE)
While the methodology of FE might be similar to that of Fully Homomorphic Encryption(FHE), it has some differences. If the requirements of Bob are the same(to get the value of a+b), in the case of FHE, he would be allowed to compute the addition function on the variables a and b. But, the result generated in this case would be an encrypted form. So even if Bob didn't access the decrypted variables, he would still need the key to decrypt the output which he got from his function. Whereas, in the case of FE, the result would be the actual answer 8(i.e. a=3 + b=5).
Encryption: c = f(m, pk)
Decryption: x = f(c, f'())
where,
m = message or data
c = cipher text (encrypted data)
x = encrypted output of function f'()
f'() = any function
pk = public keyThe better one: FE or FHE?
Both methods have their designated use cases. While FHE adds an extra burden of decrypting the final output, it allows the user to select any function to compute on the data. On the other hand, FE provides the user with the decrypted output but may be restricted with the type of function to be used by the owner of the data.
Use cases for FE
This control over which functions to allow to be computed on the data that to my which user, benefits the owner of the data in multiple cases.
- If someone wants to classify their emails as spam or not spam, they may pass their email in the spam filter. But the spam filter gets access to all their email content. To avoid this privacy breach, the user can set up a Functional Encryption system where the function f'() is a user-specified program that generates the output as 1 or 0 depending upon whether the email is spam or not. So, the user can then generate a key for the function f'(), and the spam filter can use this function to output the category of the email without learning anything more about the actual content inside.
- If some suspicious activity is observed inside a company, e.g. the presence of malware, scanning the logs would make things more clear about how the malware got into the system. Now, sharing the logs with an external expert may allow them to access the company's entire network data, even if they are encrypted. In this case, a function can be generated to look at the activities at only TCP port, and the corresponding key can be provided to the expert.
Sources
The content is inspired by the paper: Boneh, Dan, Amit Sahai, and Brent Waters. "Functional encryption: a new vision for public-key cryptography." Communications of the ACM 55.11 (2012): 56-64. (You can find this paper here)
Interested in knowing more about FE? This talk will give you more information about FE, along with its drawbacks and how it can be resolved using Multi-input FE.
You can also know more about the recent advancements in FHE by IBM here.
This is a great blog which explains the working of Homomorphic Encryption.





